Purpose and Introduction
Hi, this is Skunkwerks-type-personage, and herein I'm going to try to archive or "inter" if you will, a wealth of information regarding Keyloggers and other Account Security issues that I usually keep freshly updated in a thread in the Official Earthen Ring Realm Forums.
I will in all likelihood continue to maintain the thread, but I would like to keep an archived copy here not only for reference of others, but also myself. It takes a good deal of effort to get a thread stickied, and the information changes so often that it needs to be "freshened" periodically (reorganized and such) to keep it convenient and readable. Here of course you also have advantage of the Wiki-Formatting's Table of Contents- which should make the article (a long read to be sure) easier to access for those looking for specific topics within it.
In any case, I understand it's a bit "off-topic" but as this is the Earthen Ring Community, and I've been keeping this as a service to that community, I think you can see where this "fits". --SkunkWerks 05:24, 6 December 2008 (UTC)
Blizzard has it's own Forum Dealie Explaining some aspects of account theft and such as well that's worth a read through.
Motivations
Why do Account Thieves do this? Well, as one poster on the forums once put it: "You will never see such industry in the art of account theft as you will in WoW."
And when you think about how successful WoW has become as an MMO (it's an anomaly in the MMO genre- few MMOs break the six-digit subscriber mark, let alone do so hundreds of times over as WoW has), it becomes easier to understand why there is such "industry" in the account theft trade. To put this simply: there's a lot of money to be made.
When an account is taken over, the thieves who take it are generally seeking to do two things:
- 1) Fleece the account for all it's worth- selling off all equipment and stored goods, or transferring them to other accounts quickly so that the more protracted process of auctioning valuables can be conducted- in an effort to make as much gold from the account as possible.
- 2) Further the trade of account theft- to which end these stolen accounts will be employed to post URLs leading to keyloggers, trojans, false "login" pages and whatever other deceptive tools the thieves may be using to facilitate account theft. In this sense, like a virus, it invades the "cell" (account) and reproduces more of itself by phishing for new marks who will in turn have their accounts stolen, and so the process begins anew.
Show Me Tha Money!
This leads to the question of where all that stolen gold and property goes- if this is a business, as I've suggested, someone must profit: who? To answer that question, we have to look at two sorts of WoW-related URLs- links you will see posted both on the forums and in-game. The first is the Keylogger URLs, and the second is Gold Sellers (or RMT- for Real Money Trade)- those who sell gold, "powerleveling" and other in-game "services" for real-world money.
First let's take a peek at our shadowy antagonists in this tale- the Account Thieves. What do we know about them? Well, most of the Keylogger URLs can be traced quite easily by a widely available web-based service called "WhoIs" which any internet user can make use of freely. Such traces will easily reveal who registered a domain name (the central part of any URL) and where that person hails from. These traces nearly ALWAYS lead to a Chinese origin.
Now let's look at Gold-Sellers. This is obviously an attractive offer to many players who feel they do not have the time for the "grind" that playing WoW can in many ways represent. You fork over a bit of cash and in return, get someone essentially to play the game for you- either by giving you goods or gold you never truly earned, or "powerleveling" your character- a term which basically means leveling a character very quickly.
What do we know about gold sellers? Just as you can trace Keylogger URLs via widely available services, you can do the same for Gold-Sellers. And in any case, it's not exactly a secret that most Gold-Selling outfits (and the "gold farmers" they purportedly employ) are also Chinese in origin. We also know that Gold Farming, as many "insider" articles will tell you is a very formidable task, and a highly time-consuming activity. The individuals "hired" (it's been oft demonstrated that many work for a pittance- which is not necessarily unique to the MMO RMT "industry" in China in any case) work long hours, and work like machines.
The Devil is in the Details (A Different View of Your "Friendly Neighborhood Gold Seller")
Aside from the Chinese origin, what other similarities could we find between these two parties?
Well, neither business is "welcome" as far as Blizzard (WoW's parent company) is concerned. They operate in a shady area outside of Blizzard's Terms of Service- which is a legally-binding document that all who play WoW- be they players or gold-sellers- must agree to in order to play (be provided service). Blizzard has shown a history of actively prosecuting RMT companies wherever it can- most notably forcing an injunction against once-popular RMT company Peons4Hire on the grounds that it's incessant spam of global chat channels as well as whispers to players was creating an adverse experience for players and damaging Blizzard's business.
And obviously Blizzard doesn't want Account Thieves running willy-nilly, making a lot of sad and inconvenienced players and ruining their business that way- so here's another group of individuals who operate in a very small margin- which basically consists of wherever they can worm their way into unnoticed or unchecked.
Now here's the brain-buster: What if they're the same people?
As I've already suggested, Gold-Farming is a time-consuming activity. It was once far more popular I think when Gold was harder to come by (prior to Burning Crusade and the advent of the "easy-money" Daily Quests) and still primarily depended on your ability to play the Auction House in selling materials and goods. Now however, what's the motivation? I suppose it's as easy to give Farmers accounts and let them do Dailies in the same easy fashion as players do to get gold- but you're still limited to 25 a day- and that run can be accomplished really in about two hours.
And then of course you've got to pay someone (albeit very little in China) to do this.
What if there were an easier way to get it? Maybe by say, stealing accounts and fleecing them of their gold? Then you can sell that gold to other players, and make a tidy little profit doing it for all it cost you: some (likely botted) posts on the official forums containing keyloggers URLs and a few pittance fees to register the bogus sites which don't have to be paid for for more than a month anyway.
Heck, what's to stop you from just stealing that gold from other players? You could even steal it from the very "customers" you sell gold to by unwittingly infecting them with keyloggers at the point of purchase. They'll get their gold, you get their account information, and then at some later date, steal back what you sold them so you can sell the same gold to another trusting mark and be none the wiser.
Better still, you can get them to pay for the privilege of being robbed blind!
Get Out Your Tin Foil Hats Guys...
Sound like wild conspiracy theory? Should we call Oliver Stone or maybe Michael Moore? Maybe. Or maybe not...
Remember those widely available trace services for URLs? Well, it's not a well-known but easily uncovered fact that many of the URLs used by Account Thieves and those used by RMT companies share more than just a geographic similarity- they have on many occasions, shared the same registrants, or have at any rate been eerily similar enough in addresses to suggest that fairly frequently, those selling the gold and those stealing it are the same people.
Still don't believe it? Well, as these people are already operating in violation of a legal contract, for which they can be brought up on charges in Civil Court, please tell me what's so scrupulous about what Gold-Sellers do, and what stops them from doing even more questionable things? And to them this is the "victimless crime": the players who have their accounts stolen usually go straight to Account Admin and have most if not all of what they lost restored. So, your minor pain in the tuckus = their insane profit.
This is food for thought if you happen to be one of those players who may have been lured into buying gold- not only are you supporting the people stealing others' accounts, but in a tragically karmic irony, you will most probably become the victim of it at some point in the future yourself.
But in any case, the TL;DR version of this whole missive is: there's money to be made in account theft- the same take the RMT industry enjoys. That's where all that gold goes.
Modus Operandi
Now that we've covered the "why" of the matter, let's look at the "how" of it. Returning to the statement about the amount of "industry" seen in the theft of WoW accounts, it's safe to say that the how is a veritable cornucopia of tom-foolery, cheap tricks, and underhanded schemes. Almost too many to count, honestly. But what I can try to do is identify some of the common "tools" used in the trade and how they're generally employed. First, let's look at what tools keep for, well, tools.
Tools of the Trade
Phishing
This is a specific sort of computer hacking strategy. As its trendy phonetic alteration of a more common English word (fishing) implies, Phishing suggests baiting a line and then waiting for bites from unwary fish. It is the strategy of least effort for the hacker, as it's basic premise involves tricking a user into giving you secure information. Ever seen that tip on the WoW loading screen that says "A Blizzard employee will NEVER ask you for your password"? E-mails asking you for such things (often obliquely: "please verify your account information") are attempts at Phishing. Part of the reason this approach to hacking evolved (apart from laziness) is that encryption for passwords these days is very difficult to crack. It's far easier to dupe someone into giving you that information than it is to force it from their computer.
Trojans (Trojan Horses)
This is a variety of viral code whose strategy is mostly dependent on subtlety. Whereas viruses of the past sought to do massive amounts of damage to computer systems, Trojans (like their mythologically-referenced name implies) are meant to pass into a system unnoticed and conduct their nefarious purposes in a similarly invisible fashion. Trojans can have a variety of purposes- most of which involve the unwitting puppeting of systems for nefarious purposes- but all share this "stealth" aspect in common.
Keyloggers
Probably the most common tool of these naughty men is the "keylogger". It's both a sub-variety of Trojan and part of a broader "hacking" strategy called Phishing. Keyloggers are little bits of invasive code that are designed to quietly and discreetly invade your computer without your knowledge. Once the Keylogger is in your computer, it lays dormant and silently keeps a log of everything you type. Presumably, sooner or later, you're going to enter some username/password information, and the log will record it. These logs are sent (just as discreetly) of course typically to the person who infected you and by a bit of reading, they glean secure information from them, then take your account or whatever else they can by way of them.
Keylogger URLs
A keylogger alone is just a piece of viral code. It needs a vector of transmission to reach your computer. URL stands for Universal Resource Locator, it's that odd string of text you may call a "website address" typically beginning with the prefix "http://". A Keylogger URL is a link leading to a bogus site which contains the bit of viral code that makes up the Keylogger as well as a bit of script (usually javascript) which clandestinely "injects" the keylogger into your machine without your knowledge. These bogus sites of course appear to be normal web pages, but behind the appearance is the purpose: to infect your machine. You need only visit one of these sites and you can contract the keylogger from it without ever knowing it happened.
(Website) Script
It should be noted that the same sorts of scripts that can be used to infect a computer with a Keylogger also find legitimate uses in Website design. Part of what this means is that most Web Browsers (Internet Explorer, and even Firefox) by default allow these scripts to run, regardless of the risk. The other part of what this implies is that in order to negate that risk, you must also negate the ability for legitimate websites to run script. There are certain approaches to safely browsing using scripts that involve "white-listing" sites that are deemed "safe" by the user and "black-listing" all other sites by default- allowing the user to choose what websites are allowed to run script through their browser- but any way you slice it, browsing safely means a certain degree of inconvenience for the user.
Chinese Keylogger Zombies (Stolen Accounts)
This is my own colloquial term for the posters making bogus posts with infected URLs in them. The "Keylogger" part seems pretty obvious, so let's look at the other two words. I call these posters "Zombies" because they are themselves, stolen accounts- accounts stolen by one or more of the same means I am discussing here. Think "Invasion of the Body Snatchers". These folk are sorta like the WoW version of Pod People- being puppeted by the thief who took the account. Now to the question of why they're Chinese. Well, if you look at the sites these Zombies spam, they sometimes have a ".cn" somewhere near the end of the URL string. This is the extension for sites that originate out of China. Early on, before they started getting smarter, this was an easy way to identify a URL that most likely contains a keylogger.
Spoofing
Another sub-stratagem of Phishing, this scheme involves faking the domain name or identity of a popular and usually widely trusted site such as YouTube, or IGN and attempting to use that "street cred" to gull people into a false sense of security. As with bogus login pages, these can be spotted for the counterfeits they are, but only to someone who knows what to look for, and more importantly, takes the time to look- such "spoofs" will nearly always be slightly... off in some way (a letter added or two letters transposed or replaced) since no two domain names can be perfectly identical. It only needs to look close enough to the original to do the trick. 'You1ube.com' might look close enough for someone who isn't paying much attention to begin with.
Bogus Forum Posts
There's such a variety of these that it's difficult to summarize, but the basic premise of a bogus forum post is getting you to think it's something else (most commonly pictures of naked women, free beta keys, pictures of a popular raid on Halaa, and so on) long enough for you to visit whatever URL it contains and become infected by a Keylogger without knowing it. If it seems "too good to be true" it probably is.
Bogus E-mails
If you're in the habit of passing out your e-mail address (in particular in WoW-related venues, such as the Official Forums), be aware that your Account Thief friends are watching. They will scan the forums for such bits of contact information and then you will start getting e-mails. Some claim your account is about to be closed, some claim to offer a free beta key to the latest expansion, but all will usually ask you to "verify your account information" via a login page they have most conveniently provided you in the e-mail. The login page is itself, bogus, and of course only transmits your user info to the thieves, but most of these pages are done up to look very convincing- using official Blizzard graphics and all of that- there are ways to see the counterfeit, but they're hard to spot for the untrained eye, and of course require a certain presence of mind to look for. ( http://forums.worldofwarcraft.com/thread.html?topicId=965511383&sid=1)
Bogus Login Pages
This I suppose I could have filed under Websites, as it is a form of website, but it's a fairly specific type and I see it so often that I feel it bears its own mention. HTML- the code that forms the backbone of the World Wide Web- does have some "hidden" aspects to it as I discuss elsewhere in this article, but it's actually very user-accessible by nearly anyone who knows how. I could, as Joe Schmoe user, download any webpage or site I like, then upload it to my own hosting service. I could even re-purpose the code of the page to do something other than what it was originally intended to do, yet look exactly the same. And that's precisely what this sort of scamming tool is. It is a fake login page, made to look in every way like the real McCoy, yet instead of logging you into anything purposeful (and it's very possible they might have gone as far to make whatever you get from "logging in" look purposeful as well), it takes your user name and password and sends them to an Account Thief.
I've repeated the Blizzard Mantra several times in this diatribe: "A Blizzard Employee will NEVER ask you for your account information". And it's true, they won't. They already have it on hand anyway, else they wouldn't be able to verify your identity each time you log in. But if you're thinking that an Account Thief is just going to Whisper or e-mail you asking "Hey Mr. Smith! Can I please have your username and password?", you're probably in for some disappointment. Knowing that a bald question like that would set off alarm bells, account thieves have instead opted to "ask" in a very evasive manner, this bogus login page is a commonly used way to do so. You think you're logging in, but what you're really doing is answering the Thief's question.
Often you're directed to "login" at these bogus pages by e-mail, and the Thieves will even go so far as to make the URL they provide look as if it's the legitimate Blizzard site, yet the code behind the hypertext sends you to their bogus page (for more on how that's possible, see this), if you're not paying attention, the bait and switch passes right over you and before you know it, you're disseminating your account information to nasty individuals. Sometimes these bogus login pages are also provided to you in in-game whispers. There it's not possible to hyperlink in chat, so the text they provide MUST be the real address of the site they want you to visit. Knowing that you may recognize a forgery there, they've done their best to register domain names that at least appear to be legit, even if they aren't. Fortunately there's still ways to spot this if you're attentive and know what to look for.

They isss... Trrrricksy my Prrrecious!
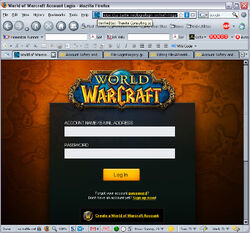
The Real Blizzard Login Page, Accept no Substitutes
To the right is a picture of an actual bogus login page I was directed to (it's thumbnailed so you'll have to click on it to see it clearly) by a whisper I screenshotted a bit later in this page, complete with annotations as to what is wrong with it and how you can tell it's bogus. I'll go over them here as well.
- The URL clearly isn't the Blizzard Official Login address. For those of you who don't know it by heart (and I imagine there's a lot of you since I don't either), it's this: https://us.battle.net/login/login.xml
- There are some additional letters in the URL, and while they're pretty in tune with what a Blizzard address might look like, they're not close enough. This picture is actually a poor example of added letters in URLs If the thieves had made a better attempt at emulating the actual login, they might have misspelled some actual element of the legitimate address to create a new domain. This is what I described earlier as Spoofing a URL.
- I had said in the annotations in the image that Blizzard should be using a .com extension to their website URL, but it seems that the legitimate Login as noted above is in fact a .net (I'm not all-knowing after all). So a point to the Account Thieves for fairly accurate emulation there. However it's still worthwhile to mention that at least in most cases, legit Blizzard pages would be using the corporate .com extension rather than .org, .biz, .us, and of course .cn. And of course there's still other signs to point out as well.
- It's not a secure server. If it were it would be preceded by "https://". It's not. This is important since any legitimate login page would use a secure server, and not any idiot can apply for a security certificate to make one. This rather locks out the possibility of an account thief getting a secure server to host this crap on.
- In addition to the raw text of the URL, many browsers will often give some visual notification when you are entering or leaving a secure site. IE uses a lock Icon that, last I knew was located on the browser's status bar on the bottom. Mozilla Firefox places that sort of Icon just to the left of the URL in the location bar. You may even notice that the formatting in this Wiki places a Lock Icon after the URL, but that's specific to this page only, and I wouldn't count on that being reliable in the text of pages. The best way to determine if a server is secure is to read the URL carefully, as pointed out above.
Posted to the right also is a second Screenshot showing the real Blizzard login page (realize that they do change the formatting from time to time and so this is subject to change in the future very probably. As of the writing of this, 6/30/2009, this is the formatting). You can see how it both looks almost alike, and yet the URL details are VERY different. When I moused over the space with the BattleNet Icon (Print Screen won't capture the mouse pointer), you may also note that it supplies me with who verified the site's security certificate in a small popup.

The Whisper Scam "Wall 'O Shame"

If you do get an Official whisper, this is what it looks like...
Bogus Whispers
These are probably among the easiest to spot. If you're familiar with the way Blizzard runs its promotions, then you should know already that they don't pester players in-game with whispers advertising things. You might get a system message about an in-game event or some such, but not whispers. People pestering you with whispers is a strategy far more common to gold-sellers and their very close (kissing) cousins, account thieves. In any case, unless you know the person who is whispering you with a link to a website, assume it isn't legit. Mind you, the person trying to trick you will often do so by trying to seem legit, naming himself "Blizza" as the picture on the left shows is a good example. Other obvious signs in the picture on the left is the terrible English- "Blizzard is about to launch a new mounts".
Hacking/Compromising "Third-Party" WoW Websites
While Blizzard's Official Site for WoW obviously "spared no expense" with regard to security, and is locked down pretty damn tight, there are a number of "third-party" sites dedicated to WoW which are run on a much smaller budget, and are thus easier to compromise and turn to less-than-charitable ends. Such sites include Knowledgebases (such as Thottbott and WoWHead), Addon Distribution Sites (such as Curse Gaming and IncGamers), and even Strategy Sites (like ElitistJerks or WorldOfRaids). Not all, but many of these sites I happen to know have had problems with this. They may have been hosting ads from an infected source (Thottbott was once infamous for hosting Gold-Seller Ads on it's site through GoogleAds), or hackers may have actually broken into the site and placed a viral code that was infecting one or more of the site's files (I've seen one or two Addon Sites fall victim to this- in particular with regard to their "automatic updating" programs). The moral of this story is that while these sites will often claim to scan for viruses themselves, don't count on them to be your only line of defense.
Google-Bombing (Search Engineering)
This is less of a front-line tactic, and more of a supplemental strategy, something that can augment the use of other tools, most commonly Spoofed URLs. This tactic involves engineering search results in popular and high traffic search engines, such as the one for whom tactic is named. It's long been known that certain aspects of a website can make it more relevant as a search result and therefore bring it closer to, or completely to the top of a given search using specific search terms. A famous instance of Google-bombing involved George W. Bush- then president of the US, and broadly unpopular.. A large and well-organized group of his detractors engineered search results by constantly creating web content which related the terms "George W. Bush" with the words "Miserable Failure". Once the content reached the saturation point, Google returned any search on George W. Bush with results using the term "Misrable Failure".
And, predictably, this has also been used by Account thieves to misdirect users from legitimate Blizzard pages- such as the Account Login page, or the Armory website to their own Bogus URL forgeries- forgeries which probably contain repurposed login pages that steal your user information. The answers to this problem are of course always to examine what links you're following carefully, and, wherever possible, only follow links to official pages from first party sources- such as only following an Armory link from the Main World of Warcraft Website.
Haste (Yours)
This as easily could be termed as something I like to call "compulsive clicking syndrome". It's the tendency for people to click a link or follow a URL without any thought as to what it might be or who may have put it there. This can be caused as much by lack of knowledge of the risks as it can just by plain compulsive behavior. "Ooh! A link! ~click-click!~" People often say a lot of Keylogger posts are childishly simple in how obvious they are, but the fact of the matter is they really don't need to be subtle to work. It certainly helps, but you'll still get a lot of bites without it.
Panic (Yours)
Some of the best tools for perpetrating account theft aren't highly technical or even especially sneaky. Get a person jittery enough and they'll start doing all sorts of things that they normally would not. This goes even for especially intelligent or wary people. You drop your guard for a moment, and they have you. A fine example of this is that yours truly (author of this near-paranoid missive about avoiding account theft) was gulled when he got an e-mail stating his WoW account was about to be closed under suspicion of gold selling. I panicked, and next thing you know I was entering account information into a bogus login page without even thinking.
Excitement (Yours)
Just as panic alters perception and behavior, so too does excitement. Have you noticed lately that with the Wrath of the Lich King Expansion the amount of Keylogger posting activity and bogus e-mails has been on a sharp rise? This isn't a coincidence. And it's a common conceit among people on the forums and elsewhere that only stupid people fall for scams and Keyloggers. This is perhaps half-true: excited people are often "dumber" than they might be otherwise, and easier prey for simple tricks and schemes- but they may be quite intelligent given other circumstances.
Anatomy of an Account Theft
Now let's take a peek at the toolbox in action and see how it all comes together.
- Bait the Hook - A forum post is made, a bogus e-mail is sent, gold or powerleveling is offered for money... whatever the method, something is done to trick the user into giving up his account info.
- Reel in the Phish - Keys have been logged, or account information has been "verified". At this point the information is captured and has been sent to the necessary people. As the user is probably still unaware they they've been hooked in the first place, there's usually plenty of time to glean from logs and then take control of the account at some later time.
- Loot n' Plunder - With the account safely in the wrong hands it's time to start stripping it down in much the same way a chop-shop team strips down a car for parts. Bound gear is sold off (in ages past, when there was no level cap on Disenchanting, this was often the choice made for bound gear), along with anything else that has only vendor value. It's my assumption that any material or gear stored in banks or guild banks is then mailed off to other accounts the thieves have in their possession that have more leeway to accomplish the more protracted and drawn-out process of auctioning off those materials for the highest cost possible.
- Spread the Joy (Optional) - Since you've got the account for a while longer, now it's time to make sure you use it to the fullest effect. So you take that to the Official Forums and start making many many posts with Keylogger URLs in them. It's my guess that this part of the process is botted in some way.
- Mad Haxx for Fun and Profit (Optional) - This has become more prevalent nowadays with the introduction of the Wintergrasp PvP zone, which many of you will know is an excellent source of high level crafting materials, and in particular, metal. Numerous reports of "underground mining hacks" have been submitted of late by players who have spotted Miners under the landscape (if you have Nameplates turned on, you can see them through landscape features) pinching metal nodes from what is assuredly a "safe" position. This sort of behavior of course involves hacking the game and is high-risk in terms of being reported and losing one's account. So it's no small surprise that when Our Chinese Friends choose to do this, they do so with stolen Accounts. Rather like robbing a bank and using a stolen car as your getaway vehicle.
- Cover Your Tracks - This step has relatively little impact on the victim of the account theft as it does on the process of fleecing an account (although it can often result in the original owner finding one or more of his characters transferred to other realms). What good is stolen money if you can't keep it? And since Blizzard does have logs of all character activity, you'd think it would be fairly easy to figure out where a large sum of game capital suddenly leapt off to and then simply take it back. Well, the solution to this problem is a convoluted and confusing process of transfers and small transactions in many different directions aimed at making the route of the theft more obscured and hard to follow. This process starts at about this point in the process, but likely goes on over the course of several hours or days from here.
- Abandon Ship - At some point, once Account Admin's been contacted and is on the case, you'll be forced off the account, or maybe you'll just abandon it yourself- as it takes some time for Account Admin to verify what's going on and put a stop to things, and by then you've probably long since done all you wanted to do.
- Damage Control - The user's account is more than likely restored through Account Admin, with most if not all possessions and gold put back to their rightful owner. I somehow seriously doubt that the gold or equipment is recovered insomuch as duplicates are given to the stricken player.
After all is said and done, it is an ephemeral annoyance, and the user is probably none the wiser for their journey, being unaware of where the point of infection occurred in the first place (assuming they didn't perhaps will it on themselves by using an RMT or powerleveling "service"), and similarly unaware of how to prevent a recurrence.
The Forums (and the Dangers that Lie Therein)
As I'm sure some of you will know, even if you don't participate in it directly or often, the WoW official forums are vast with many people posting all sorts of topics, some of them about the game, and probably as many, if not more, not about the game, or loosely related to it. URL Links have been passed around those forums since their inception, and for the most part, many of those things linked are innocent enough. But because of the amount of money and business involved in WoW, and because of the obvious visibility of the Official Forums, less scrupulous individuals seek to use the forums as their own tool for perpetrating Account Theft against it's denizens.
Bogus Posts

Here's a look at an actual keylogger post.
The primary method of utilizing the Offical (and other WoW-related) Forums for the spreading of keyloggers is the Bogus Post. As touched on above, the basic premise in making a bogus post is to get the average forumgoer to think the post is about something else long enough for them to be fooled into visiting the URL(s) it contains.
There are many different strategies employed in making bogus postings designed to fool forumgoers, and new sorts are developed all the time, but as with most things account thieves do, not much cleverness is actually required to get the tactic to pay off- it costs almost nothing in time and effort to make such posts, and if even a handful of people follow a given link and become infected, you've multiplied your returns considerably.
A good analog to explain this concept is the phenomenon of spam e-mail. It costs next to nothing for a spammer to send thousands of e-mails to people, so if even five people out of a thousand respond to a given spamming, you've already more than paid for the effort. These spam e-mails don't have to be clever- the sheer amount of spamming one can do for one's "dime" makes that unnecessary. The same is also true of these bogus posts, if not moreso since the accunts being used to perpetrate this are not only stolen from other players, but most probably botted when making the posts.
A Short History of Links on the Official Forums
Despite some accusations that Blizzard has "done nothing" to stem the tide of account theft and malicious posting on the forums, there can be observed a slow and deliberate trend towards safety measures that Blizzard has implemented on the Official Forums intended to blunt the spread of keyloggers through them. each change has been fairly small, and easily overlooked or disregarded, but has actually had a rather profound effect on the way links are posted and followed on the official forums. First, let's give you a short explanation of URLs (also known as 'Hyperlinks', and often simply 'Links')...
Anatomy and Function of a URL

It really IS about Goats...

OHMYGOD BEAR IS DRIVING HOWCANTHATBE?!?
The URL or Hyperlink is a subtle and often overlooked part of the greater structure we think of as the World Wide Web. Nonetheless it is essential to the framework of the Web- which is said to be "object-oriented". Hyperlinks are what allow you to move quickly from topic to topic in a given page by clicking on words, pictures or other objects that lead you to other pages presumably relating to those words or objects.
If we were to dissect a URL, it essentially contains two things:
- A location- pointing to another web page that can be on the same server (computer) as the page bearing the link or can link out to any location on the World Wide Web- these location strings are typically "hidden" in HTML code (the markup language that powers the World Wide Web) "behind" a word, picture or other object.
- A bit of text, picture or other object that serves as a placeholder for the whole text of the link. This Text, Picture or Object is clicked on to command the web browser to move to the location hidden in the HTML code behind the link.
Here's an Example Link to demonstrate the concept of linking... it's about goats. The text you see in blue (and when it's followed, in purple) is the "placeholder" ("it's about goats") while the link hidden behind the placeholder in the code is in fact "http://en.wikipedia.org/wiki/Goat". Note in the first image to the right, The StatusBar and Mouseover text are showing you the actual location the link leads to.
In the above example the placeholder text and where the link actually leads you are pretty straightforward- which is to say you expect to see something about goats, and after clicking it, you do. This is a concept which, as stated above, forms the very nature of the object-oriented approach the World Wide Web takes: click on the word "goat" and you'll be taken to a page about goats.
But what if you're a less-than-charitable coder? You could use that "hidden" aspect to link to nearly ANYTHING you wanted, couldn't you? Well, sad to say there are a number of nasty individuals out there that will take advantage of the World Wide Web to do just that. In the following example I'll link you to yet another page about goats. If you click on it, you may note that the page it takes you isn't about goats, is it? Look at the second image thumbnailed to the left, and you can clearly see that the location is not what the hypertext claims it is.
There are a lot of variations on this approach, one of the ones Account Thieves will use is to use the actual legitimate URL as a facade for the text underneath, like so: http://en.wikipedia.org/wiki/Goat. See how that works? Never assume that hypertext tells the truth about where a given link actually leads.
So What Has Blizzard Ever Done for Us?
In regards to Linking on the forums and what it can or can't hide- a lot, actually. But it's very subtle, and easily missed.
Initially on the forums, it was "anything goes". You could hide links not only behind text, but behind images, whatever. The "BBC" (Bulletin Board Code) commonly used to code forum postings (which is very similar in form and function to HTML code) allowed you to do anything in a forum post that you could accomplish in the HTML code of a webpage.
Obviously this left a lot of room for naughty people to slip about and do naughty, tricksy things with code.
Eventually the ability to link images in the forums was removed (I'm sure as much for the reason that people were displaying violent or pornographic images via Blizzard's forums as anything else) as was the ability to create standard URL links where the location a link led to was hidden behind some other text or image.
At that point you could still simply paste a link into the text of a post and the coding would make it a hyperlink to that location, but you could no longer "hide" the location string itself in coding.

A screenshot of the Warning once used to keep people safe on the forums (and, of course, absolve Blizzard of legal responsibility)
As it was realized that links to malicious things were still running rampant, Blizzard then thought to put in a redirect page to links posted on their forums that first took a user to another page before providing them access to the linked location. This page took the form of a warning, stating that the page you might be visiting could be malicious in nature (and naturally that Blizzard couldn't be held responsible for any harm you or your computer suffered as a result of visiting it).
Some months later, apparently feeling that this wasn't stemming the tide enough, Blizzard finally removed the ability to create hyperlinks in forum posts altogether. At the present time you can still post the location URL of a page in text in a forum post, but the forum code will not make that string into an actual clickable link. You can of course still follow location strings posted in forum posts by highlighting the text, then copying and pasting it into the location bar of your Internet Browser. But the heyday of clickable linking in posts on the Official Forums is months gone.
Some bits of text (primarily those contained in User Signatures authored before this change) still contain clickable URLs and seem to be "grandfathered" as it were, but it's no longer possible to create these from scratch.
It's interesting to note at this point that the Account Thieves upped the aggressiveness of their attacks on the Official Forums at that point, spamming them more incessantly with more malicious links and more insidious ways of hiding them by confusing you as to the nature of the posts they were contained in.
As an offhand note, not too long after hyperlinking was excised completely from the Official Forums, a lot of Keylogger posts being made curiously had their URL links underlined- which is a common HTML formatting for hyperlinks. Obviously this was not for function certainly as the function was just no longer possible within the confines of the Official Forums, but appears to have been intended to make links at least appear more like links- for reasons I can't possibly fathom...
Types of Bogus Posts

Anatomy of a Single-Thread Keylogger Post
As stated, there are many varieties of Bogus Postings used to gull forumgoers into infecting themselves with keyloggers. Some are more clever than others, but in the end all share the same basic purpose- to fool people into visiting malicious links. Some of the different sub-strategies of fooling people are listed below. A given post may utilize more than one of these strategies to reel in catches, as well.
- The Single-Thread Variety - this one is probably still the most common form that a Keylogger post takes and the simplest. The Zombie Account selects a forum and posts a single thread claiming to be any number of things, from naked pictures to screenshots of a successful Halaa raid or even guild recruitment posts (complete with bogus links to the "guildsite"), and so on. These threads normally have any number of fairly recognizable titles- as the Zombies repeat them quite often. Here's a brief of some of the typical thread titles that have been observed in use with Single-Thread keylogger posts.

The "Last Post" column showing a Keylogger Spammer at work.
- The (Multiple) Thread-Response Variety - A bit more insidious and subtle than the Single-Thread Variety, this one is simply to respond to a forum post (typically MANY posts) with some sort of general response that, not too coincidentally, contains a URL which leads to a Keylogger. Response posts like this will usually be preceded by short text "blurbs" meant to mask the malicious nature of the post, things like "Here's what you need", or "this is what you're looking for", and so on. This one was employed fairly broadly on the high-traffick forums like General and Suggestions and they've broadened the strategy to include some of the "outlying forums" like the Realm Forums, for instance. Another common aspect of these sorts of postings is that they tend to be made by a single poster who then "floods" a given portion of the Official Forums (like a Realm forum, for instance) with roughly twenty responses to already-existing posts in that forum. This often happens so fast that the reporting service used to report malicious posts is overloaded with calls to have them removed and becomes inaccessible for a short period of time. Like the Single-Thread Variety, the bits of text used to mask their nature are usually one of a set of commonly used blurbs- here's a list of some of those thus-far observed.
- In a forum that moves quickly, this kind of behavior might be hard to spot, but in slower moving forums (such as the individual realm forums, evidence of this activity should be fairly easy to spot. The spammer will generally make something close to twenty posts in rapid succession (though like us, they are limited to the one-post-per-minute rule), and if you look at the front page of the forum in question and in particular the "Last Post" column, you're going to see a long string of the same name. An example of this is shown in the picture to the right.
- Copypasta - This strategy can be mixed in with other forms of forum "chicanery" in order to enhance the confounding value in Bogus Posts. It started, I believe, as a means to mask what would otherwise be one of the more obvious earmarks of the individuals making these posts- the language barrier. As stated earlier in this missive, the people making these posts are primarily Chinese in origin, and have little (if any) skill with the English language. When they attempt to author posts themselves, the results are usually uniquely hilarious examples of "lost-in-translation". They look odd and tend to put the warier onlookers wise to their bogus nature. So, instead of authoring a post themselves, the Zombie making the post copies another legitimate post already on the forums (usually a popular one with a high amount of thread-views) and inserts into that post in appropriate areas URLs leading to keyloggers. Usually the sorts of posts they pick on are posts that originally contained URLs of some sort, like screenshot posts, video posts and the like- so not only do you gain a coherent-sounding framework for your bogus URLs, you also gain a convenient "cover story" for the posting of them.
- Forum Bumps and "Plants" - Also interchangeable with other underhanded means is this little (if rarely seen) gem of a strategy. Sometimes another Zombie Account will (either inadvertently or deliberately) "bump" another keylogger post back to the top of the forum. They may even attempt to dispute warnings placed in response to those posts by other users that they are in fact keyloggers. I've not seen this happen myself but I've heard it from other people that it does. For the most part, lacking the skill in conversational English to make posts in the first place, I don't think this is a common tactic, but it may be employed I think to some degree of success in the larger, higher traffick areas of the official forums (such as General Discussion or Suggestions).
- Trojan Signatures - This is a strategy I actually haven't seen in a long time. It probably fell out of use about the same time click-able URLs in the forums were disabled entirely by Blizzard. A Zombie Account wouldn't post the keyloggers in the text of it's posts, but would instead leave them "innocuously" in the Signatures that were tacked onto their posts. I'm guessing the advantage to this approach is that it tended to go largely unnoticed by forum users, and thus not reported, sadly the disadvantage was the same- fewer people bother with links in forum signatures than they do with links contained in actual posts. Again, I haven't seen this happen in a very long time. but as will all fads and fashions, they hardly ever die out completely, they just get recycled.
Other Phishing Strategies/Venues
Obviously the Official WoW Forums are the most ripe ground for Phishing. Put simply this is because you have a guaranteed audience of people who are actually interested in WoW and most likely have an active account ripe for the taking. Just as pirates lurk in places where many ships pass, account thieves are dropping their lines where they're likely to catch the most 'phish'.
But there's other ways to get at respectable numbers of WoW players, some which are almost equally attractive to the entrepreneurial account thief for various reasons. I intend to point some of these out in the following subsections.
E-mail Scams
These scams require a bit more "effort" on the part of the account thief, but not much given the careless way in which many people throw around their e-mail addresses on the internet (and other more personal information), and so it's still a great way for a thief to get at a player with relative ease. The "effort" involved is mostly to make sure you've got the highest likelihood that an e-mail address you're sending to belongs to a person with a WoW account.
How do you do this? Once again, you watch where WoW players gather. The official forums is one good and obvious place, but there's also third-party websites or WoW-related fan sites. This watching can be botted as well, there are "spider-bots"- small relatively simple programs that can scan through gigs of website pages in a relatively short period of time looking for anything that appears to be an e-mail address. That bit of text is then stored for later use.
Many third-party based sites require that you register (even if it's free) to take full advantage of the site. And this usually means leaving an e-mail with the website in question. And while it is true that most of these sites promise that they won't sell or otherwise disclose your e-mail address to anyone else, there's no real reason to trust to their scruples. If you start getting spam afterwards, it's very unlikely you'll have the savvy to trace where your e-mail was outed- particularly if you're using the same e-mail address everywhere. So once again, other than good faith and intentions, what's to stop a website from selling or giving away your address? Nothing.
Another possibility is that, despite being genuinely honest about their desire not to sell or give up your contact info, the site could become compromised and your e-mail address may be stolen from the server by force. And while Websites can be held responsible for this sort of slip-up, who really sues a backwater third-party WoW website for leaking their e-mail address, even assuming the person can prove it was their site that was the source of the leak?
And yet another possibility (probably the most common) is (your) user error. Many sites require that you consciously choose to hide your e-mail address in your profile at the time you create your account (or else this can be done later in your profile options). If you're not taking advantage of this, you left yourself wide open to whoever cares to send you e-mail.
Now, you may be asking yourself, why is any of this important? If someone sends me an e-mail that looks fishy, I'm going to toss it out immediately and not do what it says, obviously.
The first and most obvious reason is that if account thieves make a habit of being obvious, they're not going to trick many people, now are they? And the scam e-mails I've seen going around are quite clever- anyone who doesn't know what to look for has a good chance of being bamboozled.
And yet another reason relates to a much easier way to verify that an e-mail you're getting is from a legit source to begin with. Blizzard, like all sites storing user information, makes a legally-binding promise to keep your contact information private- one that if I may add is mandated by Federal law. Now after I just got done explaining why you shouldn't trust the scruples of just any site in this regard, let me tell you why trusting Blizzard's scruples in this matter is a pretty safe bet.
- As a company with reportedly over ten million subscribers, Blizzard has plenty of ways to make money off their userbase without resorting to methods which would severely damage customer trust (or possibly precipitate class-action lawsuits).
- The above-mentioned trust is made doubly important by the fact that Blizzard uses the e-mail you've given as a secure line of communication to you. In the event that your account has been compromised, Blizzard won't accept an e-mail from any address save the e-mail address you linked to your account. Try to imagine for a moment if just any person could e-mail Blizzard and say "Jane Doe's account has been compromised, and could you please change the username and password to the following..." That wouldn't be a very secure situation, would it?
So, you're probably left wondering how this relates to a relatively easy way to tell if a given e-mail you're getting is authentic. Well, if the address you gave to Blizzard for your account was ONLY given to Blizzard and no one else, then you may be pretty certain that e-mail coming to any other e-mail addresses you may have claiming to be Blizzard account admin isn't genuine.
And e-mail addresses are so ubiquitous and disposable these days that it's pretty easy to utilize a webmail account (hotmail, gmail, etc.) solely for a purpose like this. For the real security enthusiasts, there are also services which can shield your e-mail address behind any number of dummy "redirect" addresses which can be generated and uniquely handed to specific websites. One such example of a service like this is Sneakemail, but there are others.
Is This E-mail Authentic? (Strategies used to fool you)
Aside from the virtues of using unique e-mail addresses, there are other signs that could put you wise to the notion that someone is trying to have one over on you.
"Verify your account information" - Be wary of these words in any e-mail, not just in WoW-related ones. It's an age-old phrase that's been used to gull people out of personal information. The basic premise is that they need to make sure you are you. Think about this a moment. They already HAVE your username and password stored on their servers. Why do they need it from you? Needless to say, this still works.
To counteract this, many advice pages on account safety and security (including Blizzard's) will tell you, "we will never ask you for your account information". However, there are a few (pretty sneaky) permutations of how they "ask" which might trip you up.
They don't say "Hey, we're Blizzard Account admin, really, we are. Can we take a gander at your username and password? Go ahead and just e-mail it to us, it's totally safe, we promise". Instead, they will often direct you to a website where you can "log in". In fact what you're doing is of course sending them your account information. The way to spot this is usually inherent in the address of the "Login Page" they send you to.
You also cannot depend on the e-mail address in the FROM field to tell you that it is in fact, from Blizzard legitimately. As of this time it is far too easy to spoof an e-mail address. And in fact unlike spoofing a URL, a spoofed e-mail address can be, and quite often is, an exact duplication of any address the Thief wants it to read as. So it will appear to come from Blizzard, yet it came from somewhere else entirely. Here are some more reliable ways to spot a fake e-mail:
- Most obvious: the address for any login page for WoW should be the proper address (https://us.battle.net/login/login.xml at the time this article was written/last edited). Some more clever attempts to fool you may contain things that look like this, but have a misspelled look or extra letters or whatever. If it doesn't look right, don't go there. And bear in mind, the hypertext of a link and the actual location it sends you to can be different. If you mouse over the hypertext, the location should show in your browser's status bar on the bottom of the window. This is where the link actually goes, regardless of where the hypertext says it goes.
- Not a secure site: Some years ago, an additional HTTP protocol was added to the World Wide Web to combat the growing attempts to steal account information. This protocol is known as HTTPS- where the S stands for 'secure'. Any site today worth creating an account on or giving personal information of any kind to uses this protocol for handling ALL user information. This protocol is also very obvious to spot when it's in use.
- Firstly, it's the beginning part of any URL for a secure site: "https://worldofwarcraft.com" as a for-instance.
- Second, Most browsers nowadays will warn you in some way that you are entering or leaving a secure site, either with a lock icon, or dialog box, or whatever.
And because not just anyone can register a secure site without supplying a lot of credentials verifying their legitimacy, it can be assumed that any site beginning with HTTPS is playing it straight with you. Any site claiming to be a login page that does not should be avoided.
Don't Panic - Aside from the technical wizardry displayed in scam e-mails, there is also a more clever social engineering element to many of these scams, and that is getting you into a frame of mind where you will be more likely to abandon caution in the first place. Two good examples of this tactic are revealed in scam e-mails I've seen are:
- E-mails claiming to be free beta keys for well-known upcoming expansions to WoW. Just before Wrath of the Lich King there were a lot of scams running that depended on this ruse. The idea is you get excited and don't pay much attention to the fact that something's fishy.
- E-mails claiming to portend grave administrative action against your account. They'll tell you that you're suspected of (oh the irony!) gold-selling or some other heinous offense and that if you don't take action, your account will be suspended. Of course taking action usually involves some form of the 'verify your account information' ruse mentioned above.
- Greetings,
- Greetings,
- An investigation of your World of Warcraft account has found strong evidence that your account is being sold, traded, or is being used to sell in-game currency. As you may or may not be aware, this conflicts with our EULA under section 4 Paragraph B which can be found here:
- An investigation of your World of Warcraft account has found strong evidence that your account is being sold, traded, or is being used to sell in-game currency. As you may or may not be aware, this conflicts with our EULA under section 4 Paragraph B which can be found here:
- WoW -> Legal -> End User License Agreement
- WoW -> Legal -> End User License Agreement
- and Section 8 of the Terms of Use found here:
- and Section 8 of the Terms of Use found here:
- WoW -> Legal -> Terms of Use
- WoW -> Legal -> Terms of Use
- The investigation will be continued by Blizzard administration to determine the action to be taken against your account. If your account is found violating the EULA and Terms of Use, your account will be suspended or terminated. In order to keep this from occurring, you should verify that you are the original owner of the account as soon as possible.
- The investigation will be continued by Blizzard administration to determine the action to be taken against your account. If your account is found violating the EULA and Terms of Use, your account will be suspended or terminated. In order to keep this from occurring, you should verify that you are the original owner of the account as soon as possible.
- To verify your identity[*] please visit the following webpage:
- https://www.worldofwarcraft.com/login/login?service=https%3 A%2F%2Fwww.worldofwarcraft.com%2Faccount%2Findex.html
- To verify your identity[*] please visit the following webpage:
- We obtain this information due to a variety of circumstances; some of which are:
- I) User generated reports
- II) A post on an account selling/trading website
- III) Sudden Internet Protocol address changes
- We obtain this information due to a variety of circumstances; some of which are:
- Only Account Administration will be able to assist with account retrieval issues. Thank you for your time and attention to this matter, and your continued interest in World of Warcraft.
- Only Account Administration will be able to assist with account retrieval issues. Thank you for your time and attention to this matter, and your continued interest in World of Warcraft.
- Regaurds,
- Regaurds,
- Account Administration Team
- Blizzard Entertainment Inc
- P.O Box 18979, Irvine, CA 92623
- Account Administration Team
- *Emphasis Mine
The above text was taken from an actual scam e-mail. One very similar to the mailing which nearly gulled me into giving up my account information to a bogus login page. As this was copy-pasted the original URL provided in the e-mail is hard to reconstruct, but what I can tell you is that in the e-mail I received, the hypertext "facade" showing for the URL actually is (or was- this predates the Battlenet login merge) the legitimate URL for Blizzard's Login page, but clicking on the hypertext used in the e-mail (which was HTML formatted, of course) actually took you to an entirely different website.
Whatever way they try to get you (and there are many) discretion, skepticism, and precautions can all help greatly in avoiding getting taken in by these douchebags. Stay alert, scrutinize everything you get through your e-mail. Don't be fooled.
AdServices and Third-Party WoW Sites
Other Means of Compromising Third-Party WoW Sites
In-Game Whisper-spam
Gold-Selling/Real Money Trade (RMT)
Getting it Back
http://forums.worldofwarcraft.com/thread.html?topicId=3773308319&sid=1
Preventing Further Thefts
Attitude
A very important aspect of dealing with this plague of Account Theft that WoW users are subjected to daily is attitude. I have myself taken a very proactive attitude towards this, though I don't expect everyone should or would be willing to play the hero here. Still it's encouraging to see other people chip in without resorting to excuses and apathy. I'll take a moment to thank each and every one of you.
"Darwinism" and Account Theft
I keep hearing this particular snarky and faux witty-sounding line of reasoning as it relates to how people get their accounts stolen, and why they "deserve" to have it happen:
- "Oh, it's okay, anyone stupid enough to fall for one of those things deserves to have their account stolen, it's like gnarly social darwinisim, dude! Like totally awesome that filly sofikul words just blew my mind, maaaayan!"
So I thought I'd take some time to comment on this subject, once:
- Darwinism as it applies to evolution dictates that the "deserving" individual doesn't get to contribute their genes into the next generation. Losing your account in this fashion, at most, means a temporary inconvenience for that deserving individual until they get their account back and anything they might have lost during the hijack- and they will.
- Darwinism implies that the "loss" of said deserving individual is a boon to the species as a whole, as it strengthens the gene pool. Well, as we already covered, the loss of an account is far from permanent, and generally few learn much from it, and furthermore the person who lost that account only really benefits the people stealing the accounts, since they go on to spread more keyloggers and other account theft schemes not only through the forums using these stolen account, but through e-mail, adservices and so forth. And it's the capital generated by this whole account theft ring that fuels the effort and thus an increase in frequency of attacks against ALL of us. Loss of these accounts (by deserving individuals or not) further inconveniences the whole lot of us by taking up the time and resources of account administration to restore access and goods lost in the theft. This is time and effort we ALL pay for.
- Losing an account to one of these scams is by no means a direct correlation to the intelligence of the victim of an account theft. Want proof of this? You need look no further than the article you are reading right now. This article on keyloggers and account theft scams was authored largely by me (I thank all of you for helping to get it stickied in the ER official Forums). Despite all my worldly knowledge of account theft- how it works, how to avoid it, and so on- would it surprise you to learn that I have very nearly had my account stolen on at least one occasion?
- Conclusion: This has absolutely nothing to do with Darwinism. And if it's anything that needs to be weeded out of the figurative "gene pool" here, it's the notion that it does have anything to do with it.
- Proposal: If you don't want to be part of the solution, don't be part of the problem. Report the keylogger, pass along word of the suspicious looking whisper, and just in general try to help your fellow community members out here. Knowledge certainly helps, but it's not the WHOLE picture. Awareness is about more than just intelligence. Even if we assume that intelligence or knowledge plays a small role here, imagine for a moment how many of your friends in this game perhaps share an account with another, like their children, for instance. Do they "deserve" this?
And if, in the end, you can't be moved to at least do a small part in fighting this, then don't make up stupid excuses to hide your all-too-apparent apathy. Letting people get their accounts stolen, wishing it on them, or spreading falsehoods about why it happens doesn't. Help. Anyone. If anything, it hurts all of us. If you're already aware of all this and you truly don't care, at least do us the favor of saying so outright and honestly.
Securing Your Computer Against Further Attacks
A Layered Approach To Security
Some of you may know of the wealth of defenive programs you could (or should) be running in order to stay safe. But why stop at one line of defense? An anti-virus program is advisable to have, but as the saying goes, don't put all your eggs in one basket.
Layers is the key here. When security measure/program fails, another picks up the slack. If we were to look at a security approach using all of the above tools, it would look a little something like this...
First Tier Security
Your First and best line of defense is (and I cannot overstate this):
- YOUR. OWN. DISCRETION.
If you don't visit the suspicious-looking URL, or enter vital information into the bogus login page or scam e-mail in the first place, we don't need to go any further down the list here. Much of the information supplied here concerns how to learn to look at possible threats skeptically, and hopefully avoid them before any of the following security measures need to get involved to save your bum.
That said, no one's perfect, and that's why such measures are still needed.
Second Tier Security
Stopping invasive threats at the Browser or Top level by denying them a means of access.
- Script Blocker (NoScript)
- AdBlocker (AdBlock Plus)
- Real-time AV Scanning (Almost any good Antivirus program)
Third Tier Security
Performing regular Scans with Antivirus and Anti-Malware programs to detect and hopefully remove anything that got past layers one and two.
- Antivirus (AVG/NOD32)
- Anti-Malware (Spybot/AdAware/Malwarebytes/etc.)
Fourth Tier Security
This consists of stopping existing but undetected and unaddressed threats from gaining access to vital resources. It could be your internet connection, as in the case of Firewalls- a Keylogger that cannot send it's log doesn't work. Alternatively (or additionally), it might be another added layer of Authentication only you possess, such as the Blizzard Authenticator- without this, an enabled account cannot be accessed with only your password.
- Firewall (ZoneAlarm)
- Blizzard Authenticator
What You Can do to Combat Account Theft
Aside from protecting yourself, there are a number of things you can do to help squash the plague of Account Theft and not only save yourself but your fellow players.
Report/Point Out Keylogger Posts in the Forums When You See Them

Note the Biohazard Icon in the upper right corner of the post. This is used to report a post.

A Screenshot of the Reporting Screen.
If you do nothing else, report any suspicious behavior that you see to the authorities- in this case, Blizzard. In the case of forum posts, this can be done using the (usually) Red Biohazard Icon in the upper right hand corner of a post frame. If the Icon is gray, this is an indication that someone has already reported it, but fear not, you can report it again, and it doesn't hurt (for the most part) to do so. Aside from reporting it again, the gray Biohazard Icon points out to you that the post may already have been deemed by someone to be suspicious.
The Biohazard Icon (red or gray) when clicked takes you to the report screen (shown in a Thumbnail to the right). This screen allows you to report a post to the Forum Moderators for a bevvy of different reasons. For a post I suspect contains a Keylogger, typically I select "Posting or linking to pornography, malicious programs, unreleased content." from the reason dropbox and just write "Keylogger" in the text box. Being that the WoW forums are large and Moderators stretched thin, this is the only sure way they're going to hear of a keylogger post being made in some obscure corner of it. And it's about the only way you can draw attention to it to hopefully have it removed, albeit not nearly as expediently as such things typically should be sometimes.
In any case, reporting these things passes that information along to Blizzard, which in turn keeps them apprised as to what's going on out there, and how best they can combat it. You might additionally respond to the post with a warning about the Keylogger to any users that may stumble on it, but often these posts are so long that it ensures whatever warning you might issue will be well-below what a user first sees when they load the thread and they'd have to scroll down to get any benefit. Bear in mind your warning response also bumps the thread to the top of the forums.
Also bear in mind that when pointing out a Keylogger, DO NOT QUOTE THE KEYLOGGER URL. If you should decide to point out the bogus post with a response of your own, please, don't quote the infected URL in the post. This may sound simple enough, but I can't tell you how often I see it. People will, often as not, visit links without reading the posts they are attached to, and by giving these scumbags one more posting space for their infected URLs, you are effectively doing their job for them. If you want to call attention to the specific post containing the Keylogger, use the number of the post- which appears along the top of the post to the left of the title. Alternatively or Additionally you may use the Name/Realm of the Poster. If you feel you must quote the post, REMOVE THE URL.
Report Suspicious Whispers/In-Game Mails
This primarily falls under the aegis of keeping Blizzard informed, the more informed they are, the better they can protect you. But yes, if you get one of these invites to ruin, like those I have spoken about above, please, please report them. Even if you only report them as Spam, it's a great help for Blizzard to know what sorts of scams are being run out there.
Report Suspicious E-mails
I've spoken above about e-mail scams already, and here again is an opportunity to help keep Blizzard informed. There is actually an e-mail address you can forward copies of these bogus mails to: hacks@blizzard.com If you see something like this, don't hesitate to pass it along to the authorities.
Report Gold Spam In-Game

In-Game Spam from Gold Sellers may come in public channels like Trade (It's called 'Tard' in my UI for a reason), Whispers, or, as in this case, a clever combination of both. Here the trade spam looks innocuous enough, but once you send a tell to the spammer, the bot responds by spamming you with an address to a Gold-Selling service.
As I've already submitted several times, Gold-Sellers and Account Thieves operate in tandem, each feeding off the other. What you do to hurt Gold Sellers also hurts Account Thieves. And while reporting it as spam may not seem like you're doing much (the flow of in-game spam will never stop so long as it's cheap and easy to do), there have been documented cases where Blizzard has utilized these reports to put Gold Sellers out of business. Every little bit helps.
It can't be said enough here that knowledge is power. The more learned we all are about this, the less likely it is that we'll fall victim to one of these scams.
Don't Support Gold-Sellers/Powerleveling "Services"
As I've already pointed out, Gold Sales and so-called Powerleveling Services provide the money that drives this whole repugnant little machine. This is the case because the people stealing the accounts and the people selling the gold they get from them are the SAME people- or else they work in concert so often to at least qualify as Aiding and Abetting. If you are buying gold, chances are you are buying gold stolen from someone else. And worse still, if you've provided these scumbags with any pertinent account information- either willfully or because their oh-so-helpful site just infected you with a keylogger or some other trojan, you could become a victim of an account theft yourself.
Account Trading/Selling, a practice also prohibited by Blizzard's Terms of Service Agreement, is another business that goes hand in hand with Account Theft. Don't believe me? A good friend of mine recently had his account stolen and posted on some German account trading site for a cool $2000 USD in the same day.
These people are not your friends, they do not care about the quality of your play experience, and they are more than happy to stab you and others in the back if it means they can turn a profit off it. Don't provide them with a market to sell their ill-gotten wares. You'll be doing your fellow players a great service by this alone.
Appendices
Herein are contained a number of informational archives on the subject of Keylogger posts. Much of this has been gathered by observations and patterns seen while browsing the forums. It is kept both for posterity and for reference and will be updated as new information becomes available.
Appendix A: Typical WhoIs Profile for a Bogus URL
Domain Name.......... <DOMAIN NAME REMOVED FOR OBVIOUS REASONS>
Creation Date........ 2008-09-07 12:40:07
Registration Date.... 2008-09-07 12:40:07
Expiry Date.......... 2009-09-07 12:40:07
Organisation Name.... Star Co.Ltd
Organisation Address. Star Street
Organisation Address.
Organisation Address. GuangZhou
Organisation Address. 100000
Organisation Address. XJ
Organisation Address. CN
Admin Name........... Zhang ShanShan
Admin Address........ Star Street
Admin Address........
Admin Address........ GuangZhou
Admin Address........ 100000
Admin Address........ HK
Admin Address........ CN
Admin Email.......... fg@gmail.com
Admin Phone.......... +86.102322111
Admin Fax............ +86.102322111
Tech Name............ taian liao
Tech Address......... nn
Tech Address.........
Tech Address......... Nanning
Tech Address......... 510031
Tech Address......... GX
Tech Address......... CN
Tech Email........... agent10782@agent.dns.com.cn
Tech Phone........... +86.7714922224
Tech Fax............. +86.7714916049
Bill Name............ taian liao
Bill Address......... nn
Bill Address.........
Bill Address......... Nanning
Bill Address......... 510031
Bill Address......... GX
Bill Address......... CN
Bill Email........... agent10782@agent.dns.com.cn
Bill Phone........... +86.7714922224
Bill Fax............. +86.7714916049
Name Server.......... ns2.dns.com.cn
Name Server.......... ns1.dns.com.cn
Note: all the bolded CN's and other indications of Chinese origin. Also know that the Domain name (which is removed from the above text) contained no outwardly obvious evidence of Chinese origin- it was a regular .net or .com, but it's WhoIs rather obviously shows where it came from.
Appendix B: Commonly-Used Single Thread Titles for Bogus Posts
This is a historic list of Titles used for Single-Thread bogus posts containing Keyloggers. They do change from time to time, but are often used and reused. Each Title has a parenthetical notation of it's probable "style" either "lost-in-translation" or "copypasta". It can be safely assumed that any post on the official forums bearing any of these titles is about 99.9% positively a Keylogger post. I will continue to add to this list as more titles come into use.
It's also useful to note that while the titles don't change a whole lot, it's not uncommon for variations to be seen on titles, for instance, changing a letter, or capitalizing something, or even just randomly adding a number to one of the titles below. I believe this may be done in order to dodge easy detection on the forums- they're aware they use a fairly limited number of post titles and thus try to make them harder for someone scanning the forums to spot and either report or remove them.
Whatever the case, if the title bears any resemblance to any of these, that's reason enough to report it.
- "Most fun with Kazzak since Reck Bomb (video)" (Copypasta)
- "Huge Alliance Raid on Halaa (w/pics)" (Copypasta)
- "The real AP IRL picture thread!" (Copypasta)
- "hello, I am the ret" (Copypasta)
- "Sex girl" (Lost in Translation)
- "do any of you show your naked wife pics to ot" (Lost in Translation)
- "Some of my teacher's naked pics" (Lost in Translation)
- "my sex teacher" (Lost in Translation)
- "Hey Kalgan, we're fine" (Copypasta)
- "FREE BETA KEY" (Copypasta)
- "Naked Woman Caught By Satellite" (Lost in Translation)
- "After school lezzies" (Copypasta)
- "i am a sexy model." (Copypasta)
- "We Are Not Much Into WoW" (Copypasta)
- "Kylie Minogue - Wow (Original Edit)" (Copypasta)
- "World of Warcraft Girl Rants: Alliance" (Copypasta)
- "Drunken Dwarf Milita Recruiting for WotLK" (Copypasta- mimicking a Guild Recruitment post)
- "Shapeshifting proposals (Again, with pics)" (Copypasta)
- "Post your UI" (Copypasta)
- "Ret 11k in one GCD" (Copypasta)
- "I marrid with my husband todoay~!" (Copypasta)
- "Fallenman Goes Emo" (Copypasta)
- "the most sex woman in the world !" (Lost in Translation)
- "Angelina Jolie sex on legs" (Lost in Translation)
- "Wii Sex Toy" (Copypasta)
- "Welcome To Being Dead! DK Starting FAQ" (Copypasta)
- "MIC Group Wed 24th 8pm PST" (Copypasta)
- "Bosse solo t?ten" (Copypasta)
- "audrey bitoni - school girl" (Probable Copypasta)
- "How do i beat off a rogue?" (Probable Copypasta)
- "Free Sex Video!" (Lost in Translation)
- *NEW* "Everyone to look at this crazy girl of Warcraft" (Lost in Translation)
- *NEW* "Sex angel in the Pool?" (Lost in Translation)
- *NEW* "Morris comparable to a master map sex offende" (lost in Translation)
- *NEW* "f.uCk School Bus Girls" (Lost in Translation)
- *NEW* "You've never seen so beautiful woman hospital sex" (Lost in Translation)
A "lost in translation" post usually results when our Keylogging friends attempt to author a post themselves. Being primarily Chinese, and having almost no skill with English, these posts generally look fairly odd to the onlooker. Such hilarious grammatical oddities as the "Sex Leg" and "Sex Girl" type posts have some about from these attempts. In the mentioned cases, they apparently don't understand that the word "sex", when used as an adjective should end in a Y- i.e.: "Sexy". Sadly the average literacy and communications standard on the WoW forums is not especially high in the first place (even among English-as-a-first-language speakers), so these red flags tend to go unmarked.
A "copypasta" post is one strategy the Account Thieves have employed to get around "the language barrier" in order to look more legit and gull more people. The approach is simple: find a popular legitimate post already on the forums (one with a high view count) and copy it, then insert URLs to Keyloggers at appropriate points in the text of it. Posts chosen for this re-purposing are generally the sort of posts which would contain links to things like pictures or guildsites. So not only do you get around the language barrier, but you also get a free "cover story" for your keylogger URLs.
Appendix C: Common "Blurbs" used to Mask Bogus Post-Responses
Just as Single Thread Keylogger posts share a fairly common set of titles, so too do the typically-vague "blurbs" of text used to mask the malefic nature of Keyloggers posted in response to already-existing threads. This is a short list I've compiled that I will add to as I see more of them. If a URL is seen preceded by one of these, it's a good chance it's a keylogger.
- "this is what you're looking for"
- "Here's what you need"
- "This is a joke, right?"
- "That's a good idea"
- "just beautiful!"
- "It's too good to be true!" (my personal favorite)
- "Can't do that!"
- "Oh yeah."
- "really?"
- *NEW* "It's cool!#!"
- *NEW* "i am 80 level~!~~~~~~" or "i am 80!!$!~~"
- *NEW* "Make up your mind"
- *NEW* "sexy!Girl?"
- *NEW* "naked teacher in classroom!~"
Appendix D: Lexicon and Vocabulary
Definitions for commonly-used Account Security Terms
A
Account Security
Account Theft
Account Thief
Ad (Advertisement)
AdService
AdAware
Ad-Blocker
AdBlock Plus
Addon
Anti-Malware
Anti-Spyware
Anti-Virus
Archive File
Automatic Addon Downloading/Updating Client
B
Blizzard Authenticator
Bogus E-mail
Bogus Forum Post
Bogus Login Page
Bogus Whisper
Bot/Botting
"Brute-Force" Hack
C
China
Chinese Keylogger Zombie
COM (File)
Compressed Folder
Copypasta
D
Domain Name
E
Embedding
EXE (File)
F
Firewall
G
Gold-Selling
Gold-Spam
H
Hacker/Hacking
HTML (Hypertext Markup Language)
I
Internet Explorer
J
JavaScript
K
Keylogger
L
Layered Security
A philosophy of computer security that is based on the notion that no single form of computer security is by itself, perfect, and thus should be bolstered by other 'layers' of security devices, software, and apparatuses at different levels. What is presumably not caught by one layer, is caught by another.